Natas teaches the basics of serverside web-security.
Each level of natas consists of its own website located at http://natasX.natas.labs.overthewire.org, where X is the level number. There is no SSH login. To access a level, enter the username for that level (e.g. natas0 for level 0) and its password.
Each level has access to the password of the next level. Your job is to somehow obtain that next password and level up. All passwords are also stored in /etc/natas_webpass/. E.g. the password for natas5 is stored in the file /etc/natas_webpass/natas5 and only readable by natas4 and natas5.
The information provided on this site is intended for educational purposes only. While we strive to offer accurate and up-to-date content regarding hacking and security, we cannot be held responsible for any misuse or illegal activity conducted with the knowledge gained from this site. Users are solely responsible for their actions and should use this information ethically and within the boundaries of the law.
Start here:
Username: natas0
Password: natas0
URL: http://natas0.natas.labs.overthewire.orgNatas Level 0 → Level 1
In this level we can find the password as a commentary on the html code, we can see it by pressing F12 and simply inspecting the page’s code.
Natas Level 1 → Level 2
Same as the previous level, but now you cant right click to see the page’s code, but since we are using F12 for it that’s not a problem, so… ¯\_(ツ)_/¯
Natas Level 2 → Level 3
Now on this level we have a really small image on the side of the text. We can see on the img html tag that the image is on /files, so let’s have a look on this before we go crazy on the image, to do this we can simply type http://natas2.natas.labs.overthewire.org/files.
There we can have unrestricted access to the files, including a file named users.txt, where we can find natas3 password.
Natas Level 3 → Level 4
Looking on the source code, we can see a comment that give us a hint of what we need to look for:
<!-- No more information leaks!! Not even Google will find it this time... -->“Not even google can find it this time…” so if google can’t find it there must be a way to block google to look up to some pages, in a quick search we can find some information about a file called robots.txt.
Whats is robots.txt
This file is used to communicate some instructions to search engines, that way, for exemple, we can block google to access to pages on a site. And most important of all, this files need to be on the root directory of your site.
You can find more information here: https://developers.google.com/search/docs/crawling-indexing/robots/create-robots-txt
Now we just need to have a look on the robots.txt for this level and see if we can find anything useful.
Looking in the robots.txt file we can see this:
User-agent: *
Disallow: /s3cr3t/So, the site is disallowing the /s3cr3t/, accessing it we can find the natas4 password.
Natas Level 4 → Level 5
In this level we will need to do something different that we have been doing so far. But, first tings first, let’s see the natas4 web-site first.
Here we can see the following:

Here the page are keeping track of where we have been and saying that we need to come from natas5 page, but that’s a problem, because we don’t have the right credentials to access natas5 page. BUT, we can accomplish that by simple changing the data we are sending to the web site, this is called spoofing.
What is Spoofing and how can we do it ?
Spoofing is a technique that involves changing some information before we send it to the receiver, that way for example, we can change the pages from which we came.
How can we do it?
This process may change with operating system and web browsing, but the process is very simple. For this guide i will be doing the process in a Linux machine using Firefox.
First install the FoxyProxy plugin on the Firefox and Brup Suite (Alternatively you can use OWASP ZAP).
You can find this plugin here: https://addons.mozilla.org/pt-BR/firefox/addon/foxyproxy-standard/
You can find Burp Suite here: https://portswigger.net/burp/communitydownload
You can find OWASP ZAP here: https://www.zaproxy.org/
In this guide i will be using BurpSuite, but the process is pretty much the same for OWASP ZAP
1) After you installed the BurpSuite open it, start a new temporary project and then go to the proxy tab -> proxy settings:
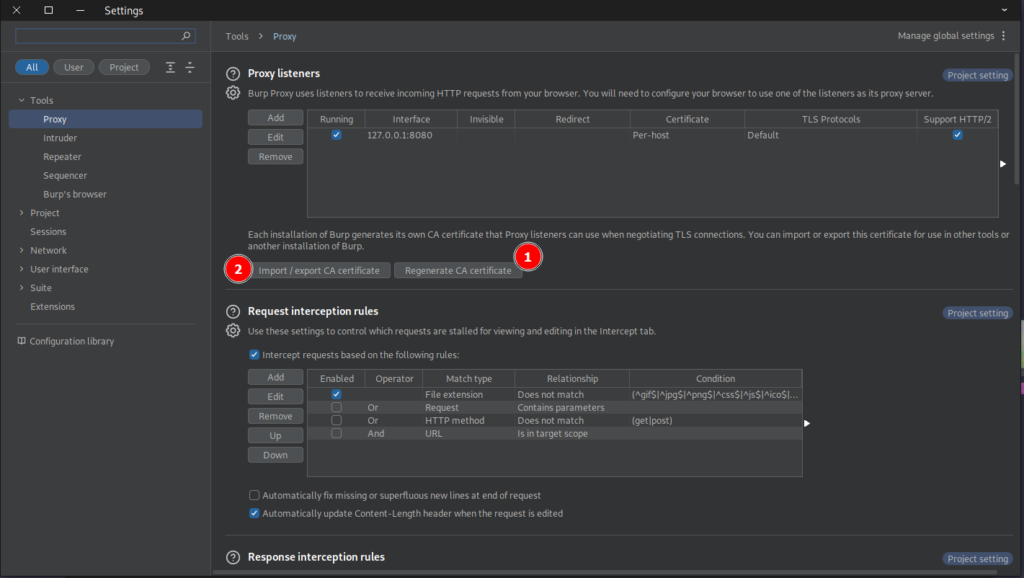
Here click on Regenarete CA certificate and then Click on Import / export CA certificate and then save it.
2) Now let’s add this certificate to firefox, go to about:preferences and search for certificates, there click on view certificates:
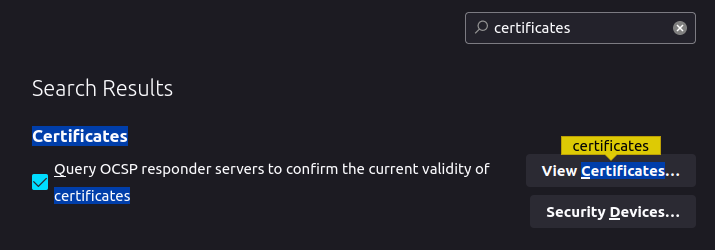
3) Now click on import and select the previously saved certificate (Mark the two boxes after):

4) Now we need to configure FoxyProxy, click on the addons tab on Firefox and then click on FoxyProxy icon, then click on options:

5) Now a new tab has opened, click on add on the right, and fill the ip, port, name field as follows:
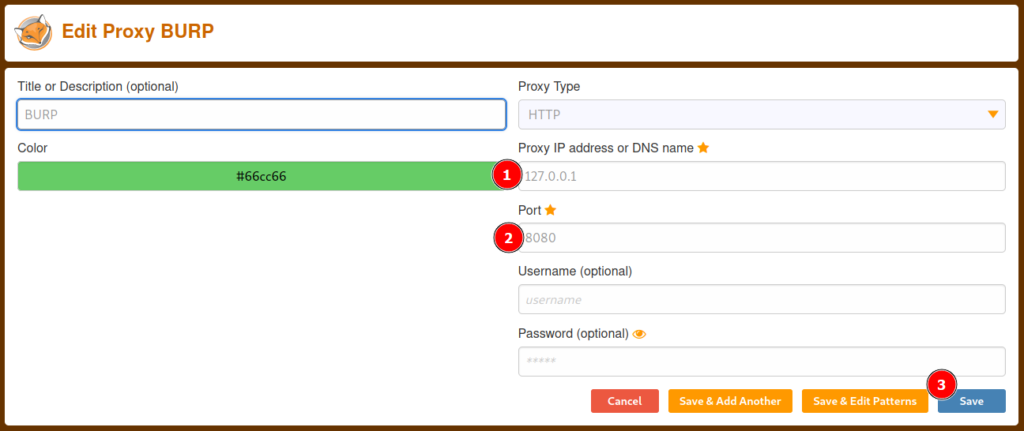
6) Now click on save and select this newly created “rule”, now everything should be configured nicely, we can return to BurpSuite and start intercepting the HTTP requests.
Spoofing natas4
Now to actually do it let’s open natas4 page again and open BurpSuite, there click on the green circle on the top, that will start BurpSuite captures.
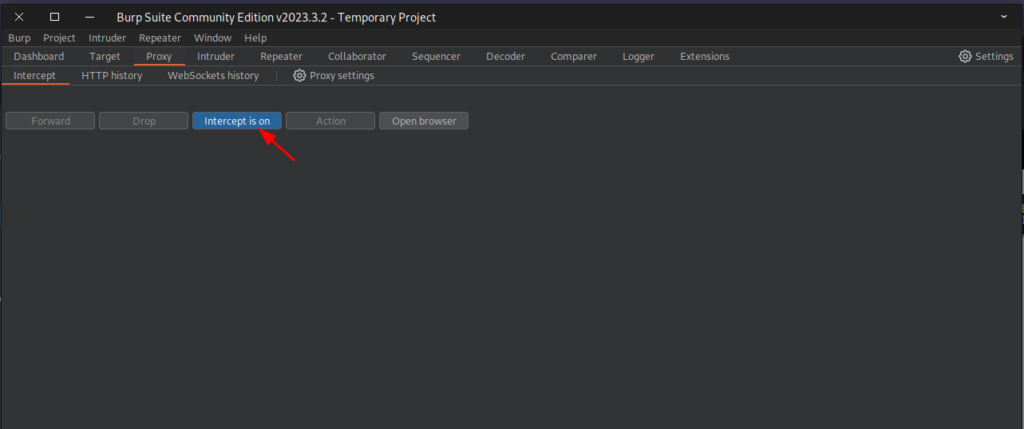
Now Let’s return to the site and refresh the page (remember to enable the FoxyProxy setting that me made). Then you will see that the page will just loads forever, because the HTML request is “stuck” on BurpSuite, there we can analise it and see what is really been sent. We can see the request on the BurpSuite, note that there is a header called refer, this header indicates from where we came from, so let’s change it to natas5:
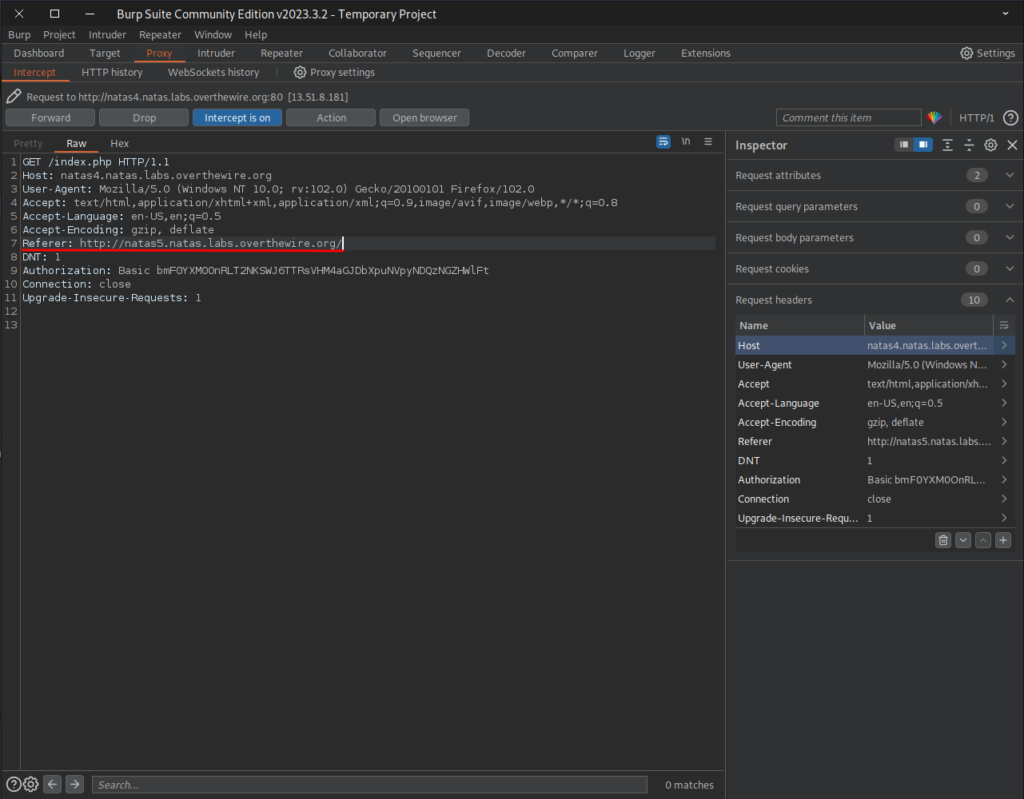
Once we click on forward we will have natas5 password.
Natas Level 5 → Level 6
Visiting the natas5 page we will see the following.

The page says we are now logged in, let’s analise the request on BurpSuite and see if there is something we can use.

Here we can see a header called cookie.
What is a cookie ?
First we need to understand that the http protocol is a stateless protocol, that means that “the application doesn’t remember who we are”, so to do that we can use a header that is typically called Cookie, that way, we can store some information of the user, so, the next time the user interacts with the application we can “remember” him.
To do tha we can create sessions ids, save usernames, passwords and much more, but there is a problem, as we saw, we can just change the cookie value.
Spoofing Cookies
We saw in the previous level that we can just change the values of a header, with the cookie is no different, after all, it’s still a header. Let’s change the loggedin cookie to 1.
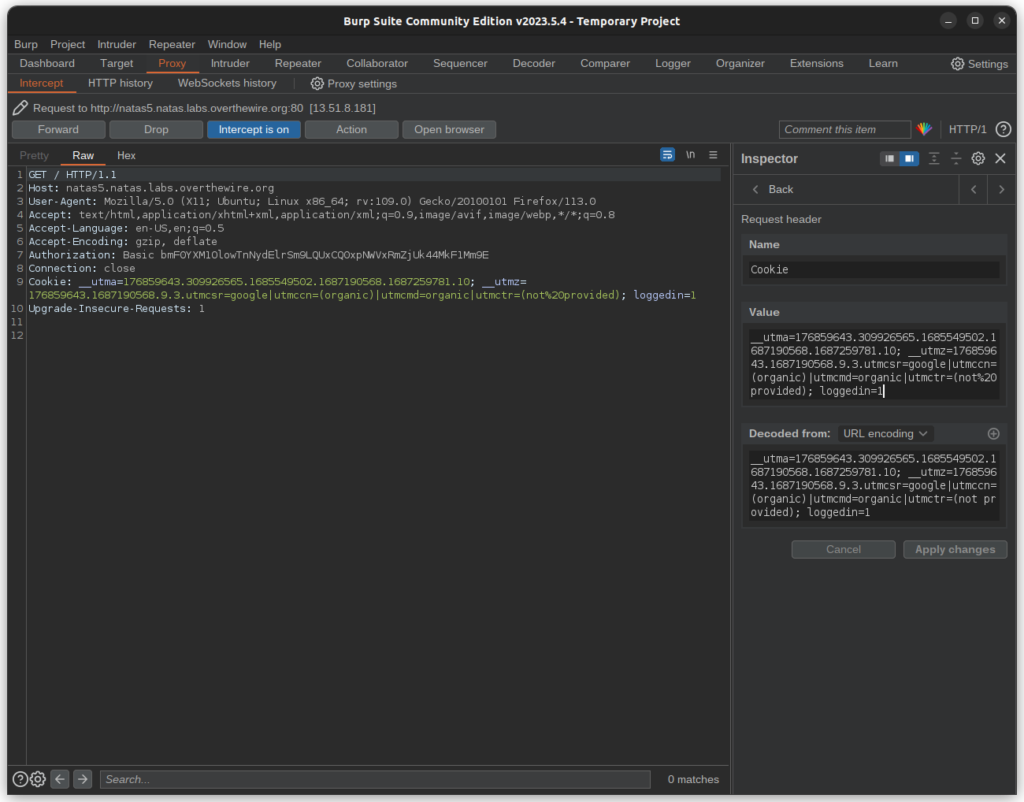
Once we forward the request we will have the password for natas6.
Natas Level 6 → Level 7
Here we have a simple page with a input section.

We can insert something in the input and then click on Submit Query to see what will come out of it. Once we do it the page return for us Wrong secret. So, let’s see what else we have here, on the same page we have a link called View sourcecode, let’s click on if and see what we have.
Once we click on it we can see the complete sourcecode of the page, but we the important part is the php in the middle:
include "includes/secret.inc";
if(array_key_exists("submit", $_POST)) {
if($secret == $_POST['secret']) {
print "Access granted. The password for natas7 is <censored>";
} else {
print "Wrong secret";
}
}If you already have some experience with any programming language you can understand this code without any knowledge of php. Here, this code is comparing what we submitted in the input field to a variable called secret, this variable is probably stored in the file that is being included in the first line. Let’s see if we can access it. Navigating to http://natas6.natas.labs.overthewire.org/includes/secret.inc we can see the source code.
There is the content of the variable secret, once we submit it in the input field we will have access to the natas7 password.
Natas Level 7 → Level 8
In this page, we have two links, one for a Home page and other for a About page.

Clicking on Home, we will be redirect to the Home page, but note the page link:

So, the php file is getting a new file to send us depending on what we click on the page, probably the home on the link has a html file associated with it. But, what if we could insert a path of a different file to it ? This Vulnerability is called File Inclusion Vulnerability.
You can read more about this vulnerability here: https://wiki.owasp.org/index.php/Testing_for_Local_File_Inclusion
On the source code of this page we can see this comment:
<!-- hint: password for webuser natas8 is in /etc/natas_webpass/natas8 -->So, let’s insert this on the page link and see if we can access the natas8 password. And yes, we can, the php has unrestricted access to system files.
Natas Level 8 → Level 9
Just as the last level we have a input field and a link to see the page’s source code, last just jump to the source right away.
$encodedSecret = "3d3d516343746d4d6d6c315669563362";
function encodeSecret($secret) {
return bin2hex(strrev(base64_encode($secret)));
}
if(array_key_exists("submit", $_POST)) {
if(encodeSecret($_POST['secret']) == $encodedSecret) {
print "Access granted. The password for natas9 is <censored>";
} else {
print "Wrong secret";
}
}Here we have exactly what we need to input 3d3d516343746d4d6d6c315669563362 BUT, there is a problem, the input field is being inserted in to a function called encodeSecret. There the input is being passed through 3 different functions, base64_encode, strrev and bin2hex. On the PHP documentation we can see exactly what does fictions do.
base64_encode: https://www.php.net/manual/en/function.base64-encode.phpt
strrev: https://www.php.net/manual/en/function.strrev.php
bin2hex: https://www.php.net/manual/en/function.bin2hex.php
So, we need to reverse this encodedSecret, to do it we can simply use all the methods used to encrypt if backwards.
3d3d516343746d4d6d6c315669563362 → hex2bin(hex2txt) → strrev(reverse string) → base64_decode
That way we can get exactly what we need to insert in to the input field to get the password for natas9.
